“Based in Porto, the 0xOPOSEC group was started by g33ks who are passionate about security. The meetup primary mission is to discuss and tackle upsurging security issues by leveraging the expertise and know-how of members of the group.”
Recon
Have_a_l00k
This first challenge was all about having a l00k(literally). They gave an URL to work with. When I opened the page I saw a video and a button.
I pressed the button and the website redirected me to another page as shown below.The new page contained a video and nothing more. I noticed that the URL was diferent so maybe that would mean something.

I decided to run dirsearch and I found a git repo with some interesting content such has index. I checked all the files, but the index was the file that caught my attention.
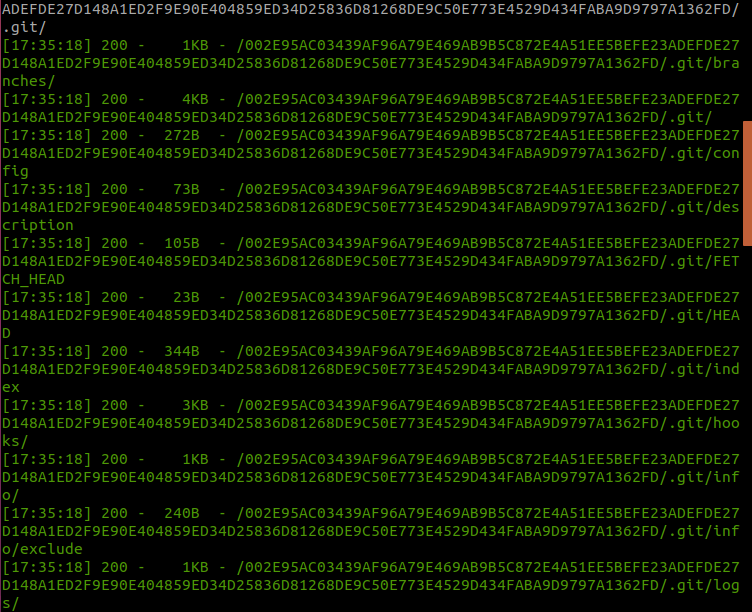
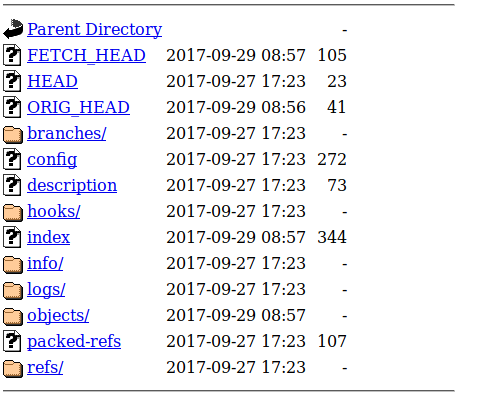
Next thing I did was to download index file to my Desktop. After that I used “strings” to see if there was anything useful for me. The result from “strings” is down below and shows us one page(8JUCv3fZ44.html).
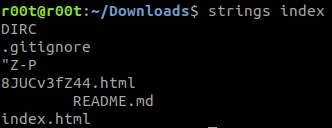
Copied and pasted the output link and then another page with a video of Jigsaw is shown. Hmmmm but how about the flag? Well, I tried to see if there was anything in the source code, and we got our flag.
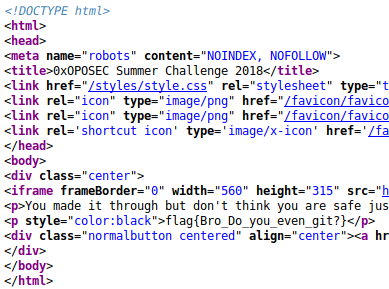
flag{Bro_Do_you_even_git?}
Misc
Lost in Translation
The second challenge was called “Lost in Translation”. I noticed why the title was called that way since i couldnt understand anything that was displayed in the challenge page. I see another video and some “random” chars.
I was confused, I looked everywhere and nothing … then I asked for some hints in Slack and they said “Programming with 8 instructions can fuck your brain up”. Copy and pasted that hint to google and the first result was “BrainFuck”.
Tricky uh? After reading about BrainFuck and understanding the problem, I simply used an online decoder and i got another flag!!!
flag{Brain_F*ck_is_Beautiful}
Reverse
Crack me if you Can
Next challenge was pretty straight forward and not that hard. The page had a video, a message (threatening) and a file to crack.
I downloaded the file and checked what kind of file I was going to work on. With file command i was able to see his format.
file crackmeifucan
I assigned runing permissions on the executable (sudo chmod +x crackmeifucan) to run it. The program asked a password, but I didnt knew what was that password so I just randomly typed qwerty. LOGIN FAILED!!! I decided to use strings command.
strings crackmeifucan
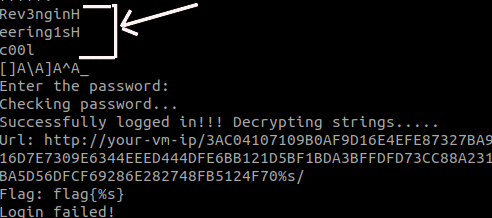
Then I cleaned that string and the final result was Rev3ngineering1sc00l. I double checked the program once again and I even used bless to see if I was right. And finally another flag!!!
flag{RevEng_FTW}
Web
We love Web 2.0
The next challenge was a Web-type challenge. They gave us a wordpress site and we had to find a way to exploit it. The site had some posts and some pictures.
I used dirsearch and i’ve found some cool stuff like a directory list but it was useless because I couldn’t extract any information from those files. Then I looked for installed plugins (since many plugins from wordpress are vulnerable) and I found akismet plugin. I tried to exploit akismet with some XSS payloads but nothing worked. Another thing I knew was that the user for the admin was “admin” since I only got the wrong password error. Next step was to use wpscan and I found a WordPress 2.3.1 - Charset SQL Injection Vuln (CVE-2007-6318).
Most database query in WordPress uses escape() method to sanitize SQL string, which is essentially filtering input via addslashes() function. However addslashes() fails to consider character set used in SQL string, and blindly inserts backslash before any single quote, regardless of whether such backslashes will form another valid character or not.
After that I injected the payload in the search field and the output looked like a md5 hash. Decoding the hash gave me the result: P@ssw0rd123. So i could finally login.
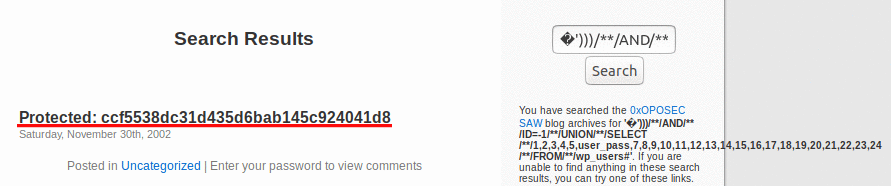
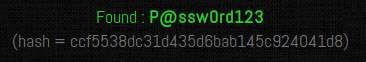
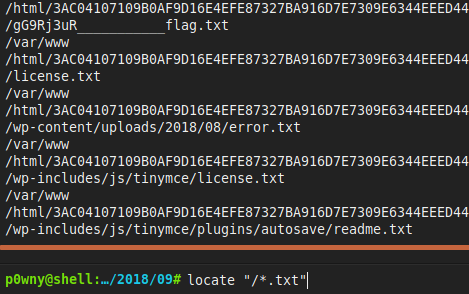
Next step was to find the flag. I looked in the backoffice but I was looking in the wrong place. After googling a bit I decided that I should upload a shell. To locate the flag I used a locate comand to find any txt file in the root dir.
I noticed that the first result was the flag so the next thing I did was use cat to see the content of that text file and move to another challenge.
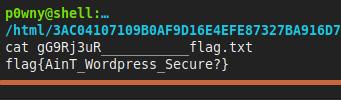
flag{AinT_Wordpress_Secure?}